Advantages
- New device authentication algorithm that drastically reduces the risk of “modeling attacks” that are a concern with PUF authentication.
- The proposed novel algorithm for communication between the device and the authentication system reduces the risk of eavesdropping on communications.
- Applicable to various devices such as cameras, touch panels, barcode readers, and more.
- The algorithm can be widely used as an authentication system for face, vein, fingerprint, iris, etc.
*:PUF:Physically Unclonable Function
Background
Authentication technology for electronic devices using PUFs (Unique Physical Function) has become increasingly popular in recently. Based on the input information (called challenge), the PUF outputs information corresponding to the “authentication key” (called response). A system authenticates the electronic devices by verifying that the pair of challenge and response is the correct combination.
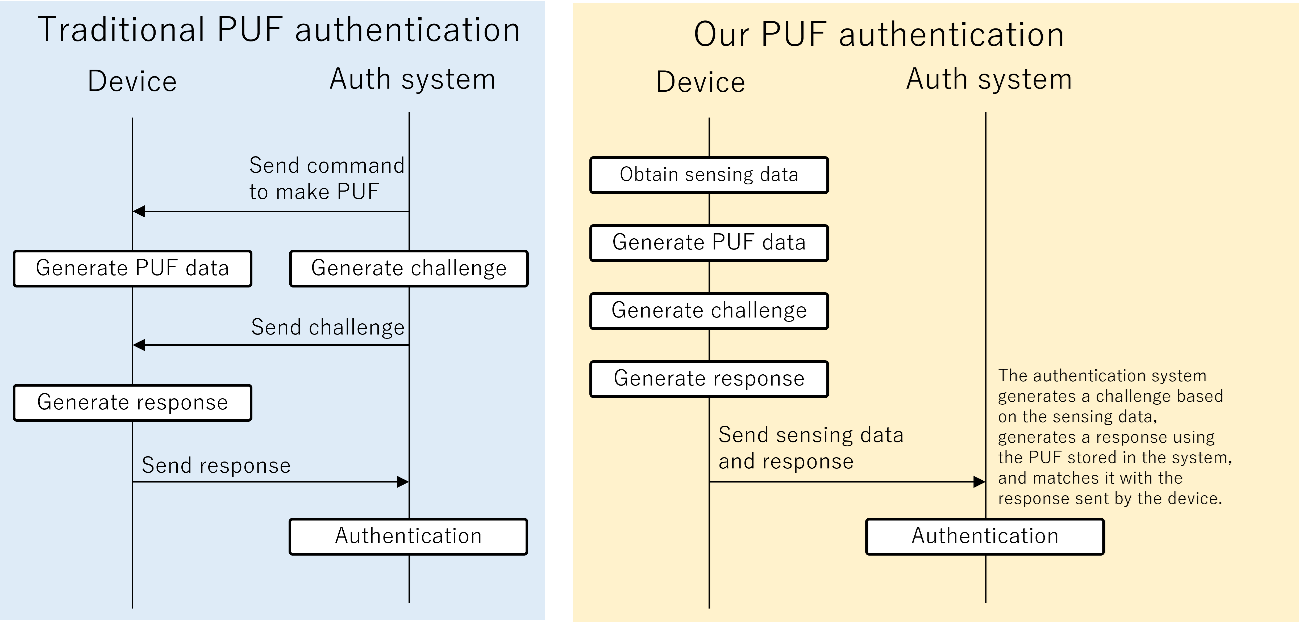
In the conventional PUF algorithm (left figure below), an authentication system generates a challenge, and a target device receiving the challenge generates a response using an internal PUF. This method has problems that impair usability, such as time-consuming communication and delays due to multiple communications for authentication. This method also poses a security risk. If the challenge and response are intercepted by criminals in the communication channel, they can use machine learning and other techniques to create a fake PUF based on the challenge and response information. This is known as a modeling attack, which allows criminals to pass PUF authentication by replacing legitimate devices.
Technology
Professor Noriyuki Miura and his colleagues at the Osaka University have now developed a new PUF authentication algorithm that avoids security risks caused by modeling attacks. An overview is shown on the right in the figure below. The important difference from the conventional PUF authentication is that the challenge is generated inside the device, rather than being generated by the authentication system. This means that the challenge is not put on the communication, making it significantly more difficult for a criminal to reproduce the PUF even if they were to steal the communication. This new authentication algorithm is expected to dramatically reduce the security risks associated with traditional PUF authentication.
The algorithm is explained as follows.
[0] A device manufacturer obtains PUF information of devices and stores them in an authentication system before shipping the devices.
[1] When a consumer tries to transfer sensing data from his device to the other devices or cloud servers, the device generates PUF information. For example, in the case of a camera device, the PUF information is a dark current data of the sensor in the camera.
[2] The device generates a challenge from the sensing data with a method proposed by the researchers. For example, the camera assigns a pixel with the maximum brightness in a camera image as a challenge.
[3] The device inputs the challenge into the PUF and obtains a response, which is an output of the PUF. In the case of the camera device, the response is the dark current value at the pixel of the challenge.
[4] The device transfers the response and sensing data together to the authentication system.
[5] The authentication system generates a challenge from the sensing data as well as the device and obtains a response to input the challenge to the PUF information that was stored in the Step [0]. If this response is as same as the response sent by the device, the system authenticates the device.
If a criminal were to steal sensing data and responses in the explained technology, would machine learning be able to predict the relationship between them? We believe that this concern can be dispelled with this technology. According to the researchers, even if a large number of challenge/response pairs generated by this technology’s authentication algorithm are trained by machine learning to predict them, the experimental results show that only the criminal obtains an ineffective model that does not work well to predict challenge/response pairs. In other words, this technology is expected to be very strong against modeling attacks.
 |
Expectation
Osaka University is searching for companies interested in developing security systems and PUF devices based on this technology. The researchers are conducting PoC research for the practical application of the technology, but we would like companies to take the lead in developing a vision for the actual use of the technology as a security system and in the development of systems and devices. Osaka university will propose to provide technical information that companies need to develop products based on this technology.
Patent & Publication
- Patent pending
Project No. DA-04565


